Deep Auth: Auth simplified

The most secure way to authenticate a user is an OTP, usually generated by an app. But in this case, OTP can be copied, stolen, or even phished. So when you’re designing your login flow and working with multiple apps to support the same login mechanism, you definitely think about how to protect everyone’s data.
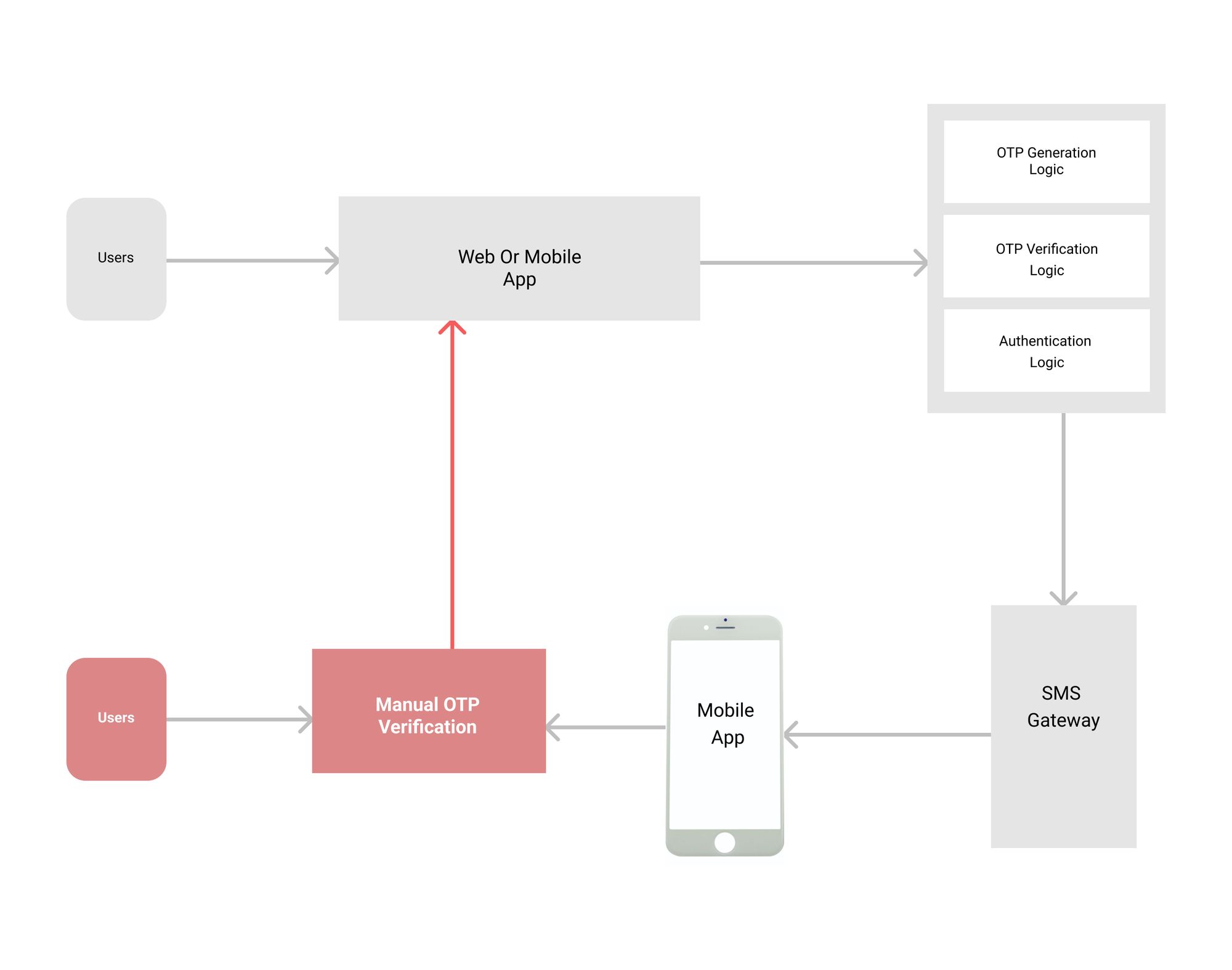
Deep Auth is the next best way to authenticate your users. OTP-based login is very insecure and not tamper-proof. Users need a system that helps them protect their own data. Deep auth helps all types of users to login into apps seamlessly. Android and apple restrict autofill OTP deep auth allows users to login into the system without entering OTP manually.
- Introducing DeepAuth: the following best-secured way to authenticate your users.
Deep auth is simpler than other OTP-based autofill systems because it’s easier to implement. Deep Auth helps all types of users to login into apps seamlessly.
As android and apple restrict autofill OTP, deep auth allows users to login into the system without entering OTP manually. DeepAuth recognizes your device as well as user input patterns and performs real-time security checks against them. - DeepAuth uses fingerprint or password-based authentication for an additional security layer.
Simply put, it’s a unique link that is then encrypted and verified by the server to protect your identity. The encryption makes sure only you can read the message—not anyone else on their end.
We can use WhatsApp or another delivery platform to connect users with our app. Deep links work on every device, so this is a good solution if we want the user experience to be consistent across platforms
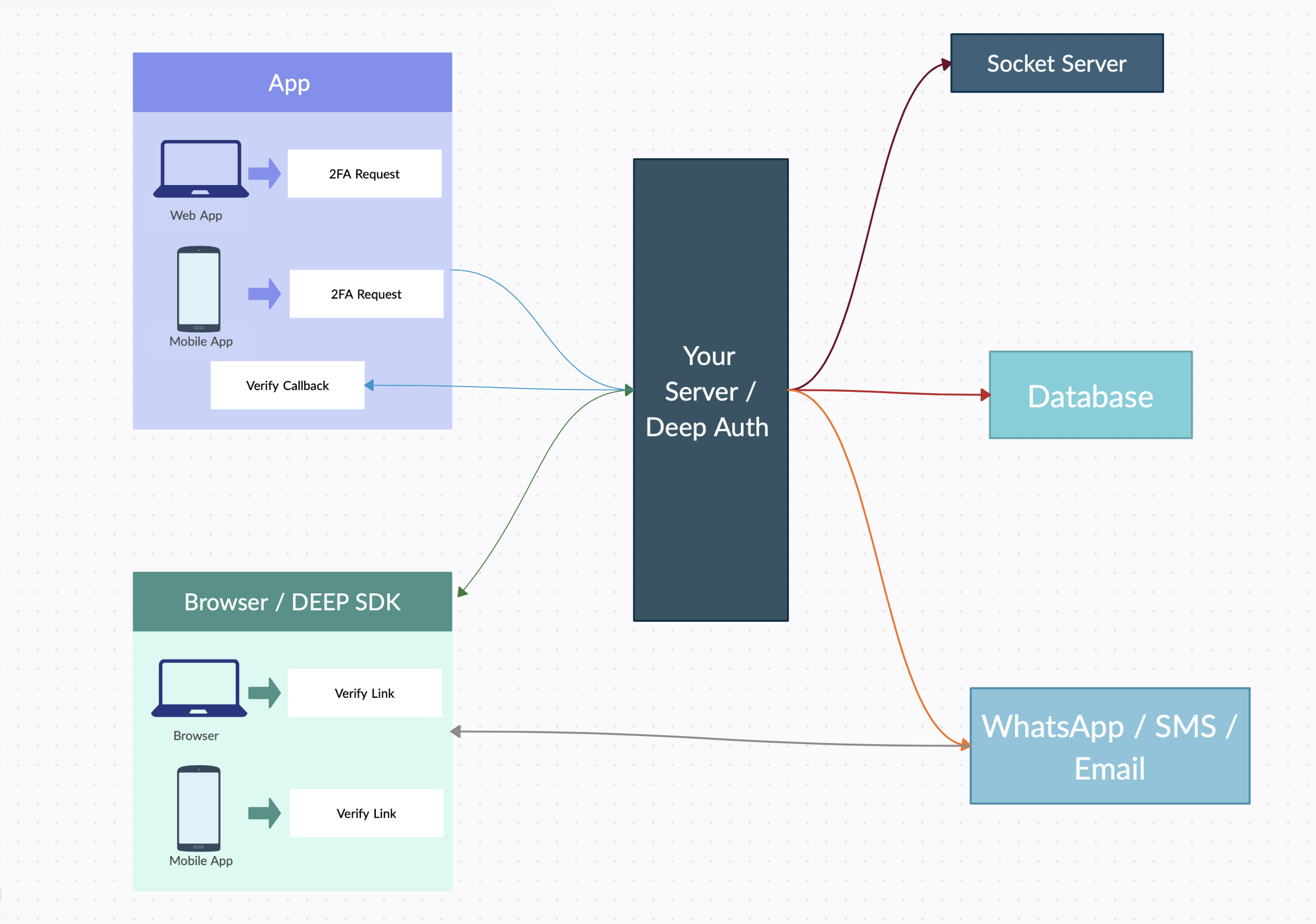
2. How DeepAuth works: authenticating users with their unique physical characteristics.
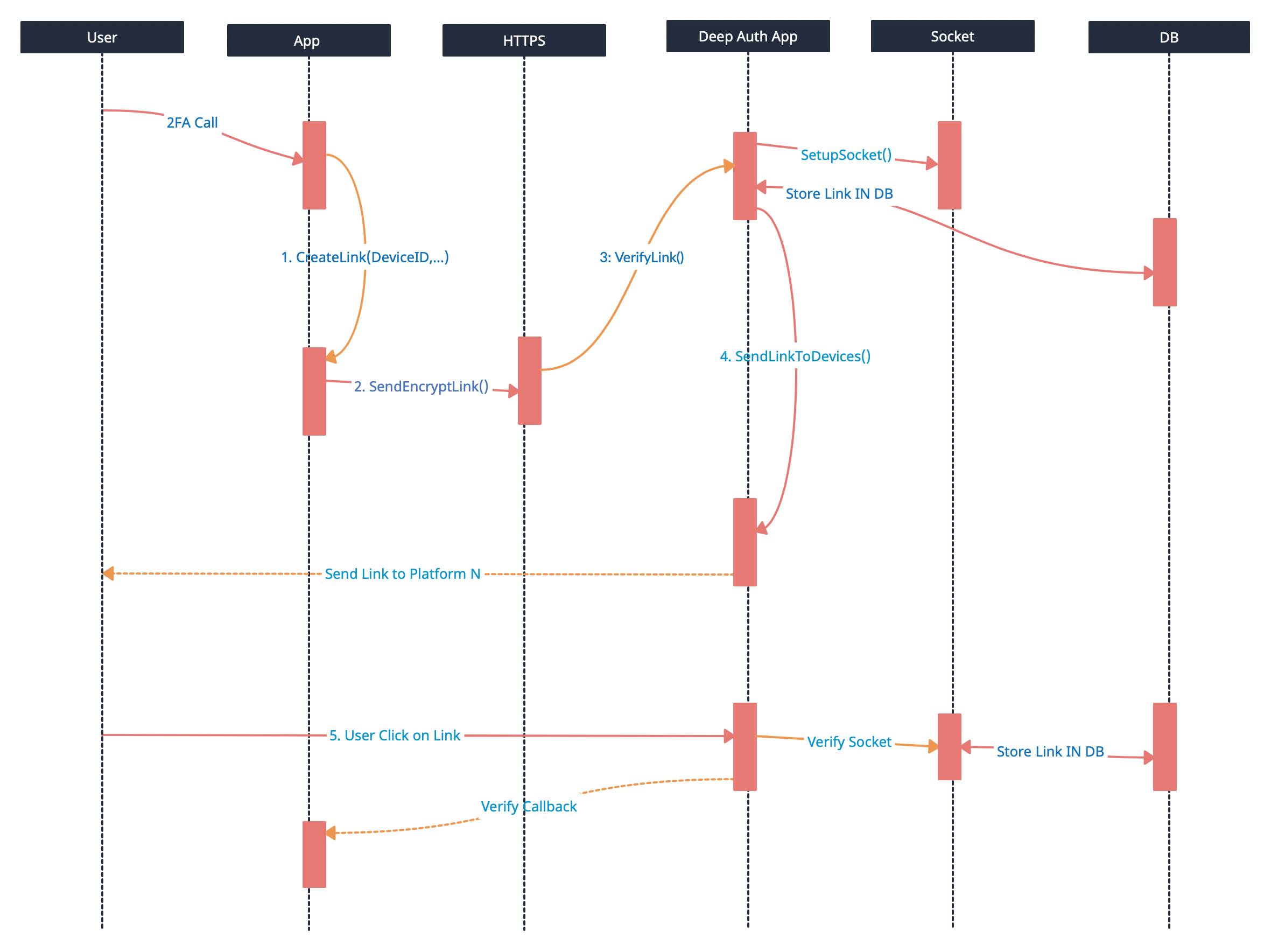
Step 1: The front will create a string based on the device id and other parameters. This string then will be encrypted to protect values.
Step 2: The frontend system then creates a deep link based on the platform
step3: Link then shared to the server to verify and confirm identity.
Step 4: The link will be then shared with the relevant platform like WhatsApp, SMS, or email verification
Step 5: Once the link is received the user can click on the link to access deep link data.
3. The benefits of using DeepAuth:
-Increased security: DeepAuth provides a more secure way to access data by using encryption and verification of the user’s identity.
-Convenience: Users don’t have to remember passwords or go through complex login processes; instead, they simply click on a link sent in an SMS or email.
-Less friction: DeepAuth is a seamless experience that doesn’t require users to go through any additional steps or fill out forms before accessing their data.
Increased engagement: Users can access the app from anywhere, at any time, by clicking on the link sent to them via WhatsApp, SMS, or email.
4. How to get started:
Adding the DeepAuth client library to your Android or iOS project and following our setup guide for your platform will help get you started on using DeepAuth in building authentication and user management flows into your application.